How To Spot a Phishing Email

Scammers use email or text messages to trick you into giving them your personal or organizational information. It remains the #1 attack vector for malicious actors. Phishing has become more sophisticated over the years. But there are several things you can do to protect yourself and TVCC. The information below will help you identify suspicious emails and what to do when you suspect one.
Phishing emails and text messages often tell a story to trick you into clicking on a link or opening an attachment.
- say they’ve noticed some suspicious activity or log-in attempts
- claim there’s a problem with your account or your payment information
- say you must confirm some personal information
- include a fake invoice
- want you to click on a link to make a payment
- say you’re eligible to register for a government refund
- offer a coupon for free stuff
- What to do with a phishing email?
If you receive a suspicious email report it to the IT Service Department. There are three convenient ways:
- Call the IT Service Desk: 903-675-6300
- Create a Service Now incident at https://tvcc.service-now.com/
- Report Phishing using the Phish Alert Button
How Can I Spot a Phishing Email?
1. Emails Demanding Urgent Action
Emails threatening a negative consequence, or a loss of opportunity unless urgent action is taken, are often phishing emails. Attackers often use this approach to rush recipients into action before they have had the opportunity to study the email for potential flaws or inconsistencies. Report suspicious emails to the IT Service Department.
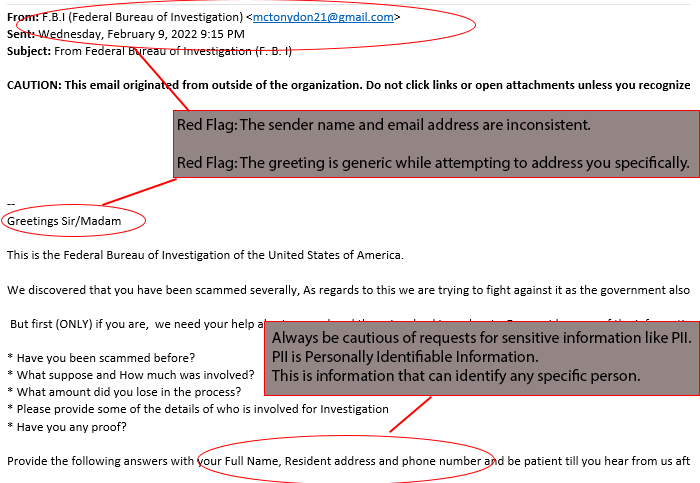
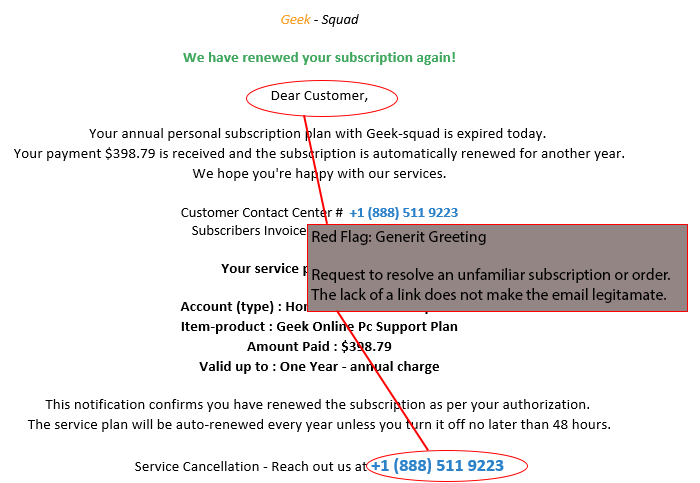
2. Emails with Bad Grammar, Spelling Mistakes, and Unfamiliar Greetings
Another way to spot phishing is bad grammar, spelling mistakes, or unfamiliar greetings. Many companies apply spell-checking tools to emails to ensure their emails are grammatically correct. Generic greetings that start “Dear,” or contain phrases not normally used in informal conversation, are often from sources unfamiliar with the style of office interaction used and should arouse suspicion.
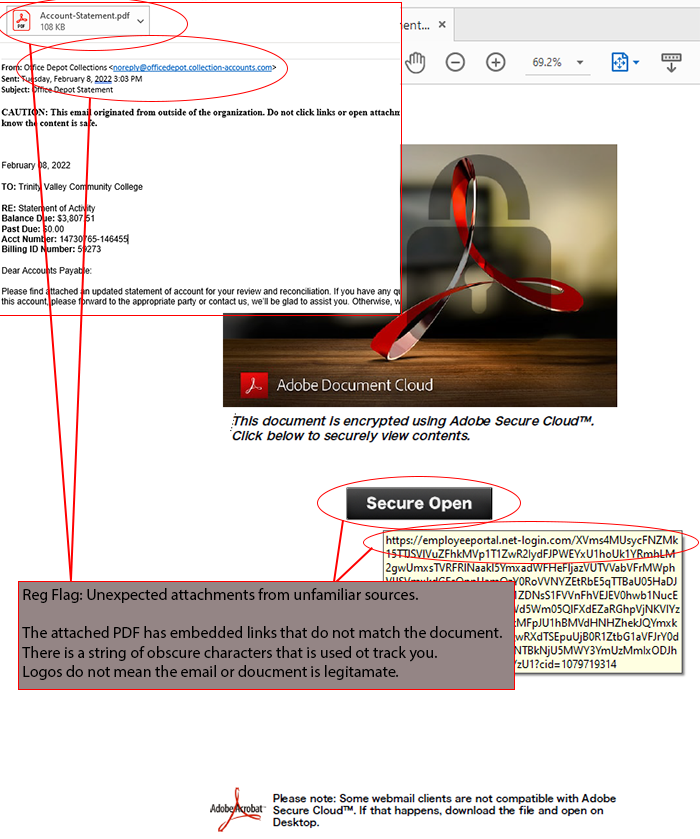
3. Inconsistencies in Email Addresses, Links & Domain Names
Inconsistencies in email addresses, links and domain names are red flags. Does the email originate from an internal address or an organization you correspond with often? Sender email addresses can be spoofed to appear from an internal or trusted source.
Look to see if a link is legitimate by hovering the mouse pointer over the link to see what pops up. If an email allegedly originates from TVCC or Google, but the domain name reads something, report the email as a phishing attack. If there is any suspicion submit the email to the IT Service Department.
Do not trust an email because of a logo. These are just images that are publically available to everyone.
4. Suspicious Attachments
Emails with attachments should always be treated suspiciously. Are you expecting the attachment? Unsolicited emails with attachments are very dangerous. If there is any doubt report the email to the IT Service Department for review.
5. Emails Requesting Login Credentials, Payment Information, or Sensitive Data
Emails requesting login credentials, payment information, or other sensitive data should always be treated with caution. Spear phishers can forge login pages to look similar to the real thing and send an email containing a link that directs you to the fake page. Whenever you are redirected to a login page or told a payment is due, refrain from inputting any information unless you are 100% certain the email is legitimate. If in doubt, report it to the IT Service Department.
6. Too Good to Be True Emails
Too good to be true emails are those which incentivize the recipient to click a link or open an attachment to claim a reward of some kind, often with a sense of urgency. If the sender of the email is unfamiliar or you did not initiate the contact, it is most likely a phishing email.
If there is any doubt or suspicious about an email or text, notify the TVCC IT Service Department. There are three convenient ways:
- Call the IT Service Desk: 903-675-6300
- Create a Service Now incident at https://tvcc.service-now.com/
- Report Phishing using the Phish Alert Button
You can also reach out to the Information Security Office with any questions, concerns, or suggestions.
TVCC ISO | iso@tvcc.edu